AWS S3 Security Hardening
(IaC + Controls Mapping)
Cloud storage seems simple , until someone misconfigures it.
I’ve seen firsthand how often organizations unintentionally expose sensitive data because a single S3 bucket wasn’t encrypted, logged, or access-restricted.
This project started with a simple intention:
to understand how S3 hardening actually works in practice, and how governance teams can evaluate controls with more confidence.
I wanted to bridge the gap between “knowing the control exists” and “understanding how it behaves in the real world.”
This case study reflects that exploration — a mix of cloud fundamentals, practical IaC review, and governance alignment.
-
This project demonstrates how to secure an AWS S3 bucket using foundational cloud security controls, IaC review, and compliance mapping.
It focuses on encryption, access restrictions, logging, and misconfiguration detection which are key pillars of cloud governance. These controls reduce the likelihood of data exposure incidents, improve audit readiness, and create clearer accountability between engineering and governance teams.This project demonstrates a practical S3 hardening approach that combines hands-on configuration review, Terraform-based controls, and governance mapping used in real enterprise environments.
-
S3 buckets are one of the top sources of data exposure incidents across industries.
Most failures happen because of:public access not being disabled
lack of encryption
missing logging
poor IAM policies
Traditional GRC reviews often say “Ensure S3 buckets are secured,” without understanding what “secured” really means. Many failures stem from unclear ownership between cloud teams, security, and governance under the AWS shared responsibility model.
This project breaks that down into technical steps and governance requirements.
-
AWS S3 security fundamentals
IAM principles
Terraform review (IaC)
Misconfiguration analysis
Controls mapping (SOC 2 / ISO / CIS)
Risk scoring & recommendations
-
1. Secure-by-default S3 Settings
I evaluated key S3 configuration requirements:
Block Public Access (ALL 4 settings)
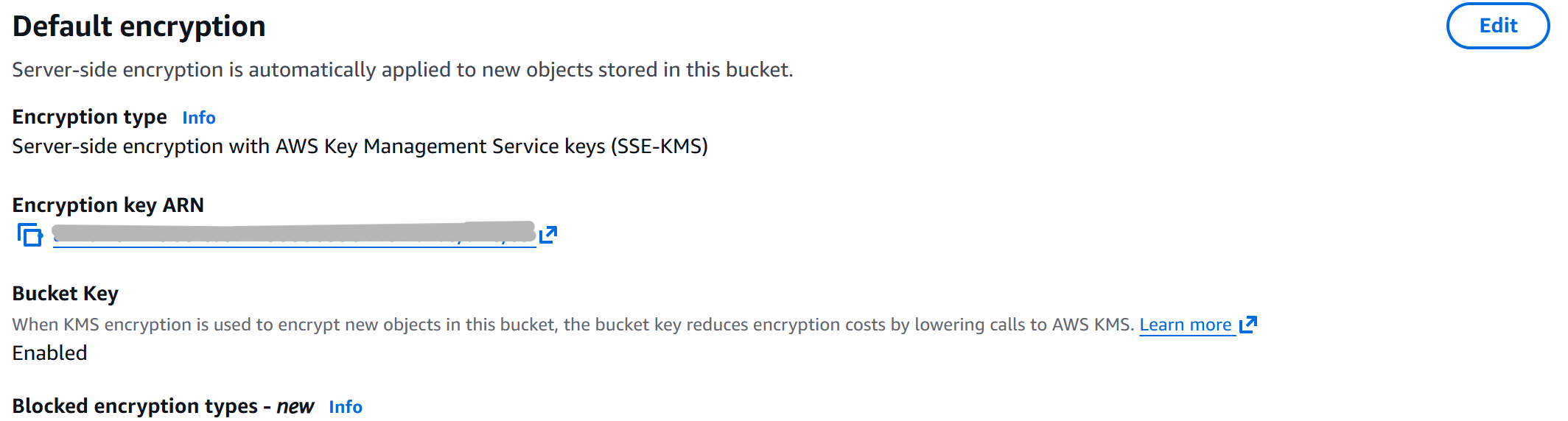
Enable default encryption (AES-256 or KMS)
Enforce HTTPS-only access
Bucket policy restrictions
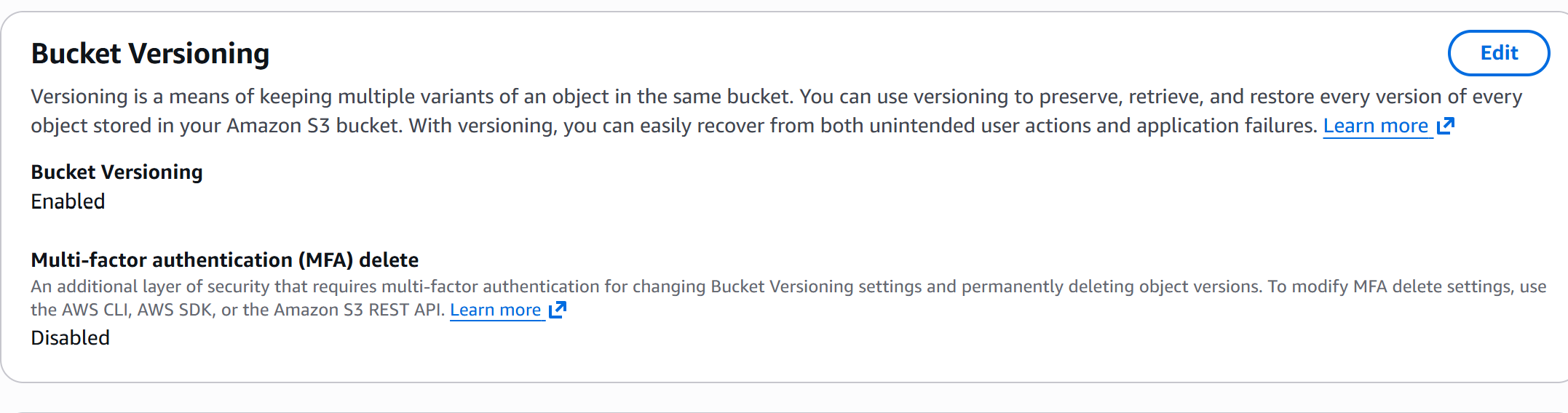
Versioning enabled
Access logging enabled
2. Terraform Review (IaC Snippet)
resource "aws_s3_bucket" "secure_bucket" {
bucket = "adarian-secure-bucket"
versioning {
enabled = true
}
server_side_encryption_configuration {
rule {
apply_server_side_encryption_by_default {
sse_algorithm = "AES256"
}
}
}
lifecycle_rule {
enabled = true
abort_incomplete_multipart_upload_days = 7
}
}
3. Misconfiguration Detection
I reviewed what happens when:
encryption = disabled
logging = off
public access = allowed
bucket policy = overly permissive
Each one introduces a clear, measurable risk.
-
Technical Controls
Enforce SSE by default
Require versioning for forensic recovery
Block all public ACLs
Require TLS
Enable logging
GRC / Governance Controls
Automate S3 checks via Security Hub or custom scripts
Review bucket policies quarterly
Require IaC scanning before deployment
Document exceptions through formal approval workflows
GRC engineering means not just saying “secure this bucket,” but knowing how it’s secured.
-
IaC snippet (above)
Risk register excerpt
Controls map
Screenshot of AWS S3 settings panel (blurred identifiers)
Governance recommendations
After misconfiguration
-
Security failures rarely come from a lack of standards, they come from a gap between intention and implementation. This project reflects how I approach cloud security and governance in practice: not as a checklist, but as a living system that must be understandable, enforceable, and defensible. By translating AWS S3 hardening into clear technical controls, mapped risks, and auditable governance decisions, this work bridges the space between engineering reality and leadership accountability. It’s designed to help organizations move faster with confidence, reduce preventable exposure, and ensure that when someone says a control exists, they can also explain how it actually works.
This approach is applicable for security teams, cloud engineers, and governance functions responsible for reviewing or approving AWS storage configurations in regulated environments.
S3 Risk Register
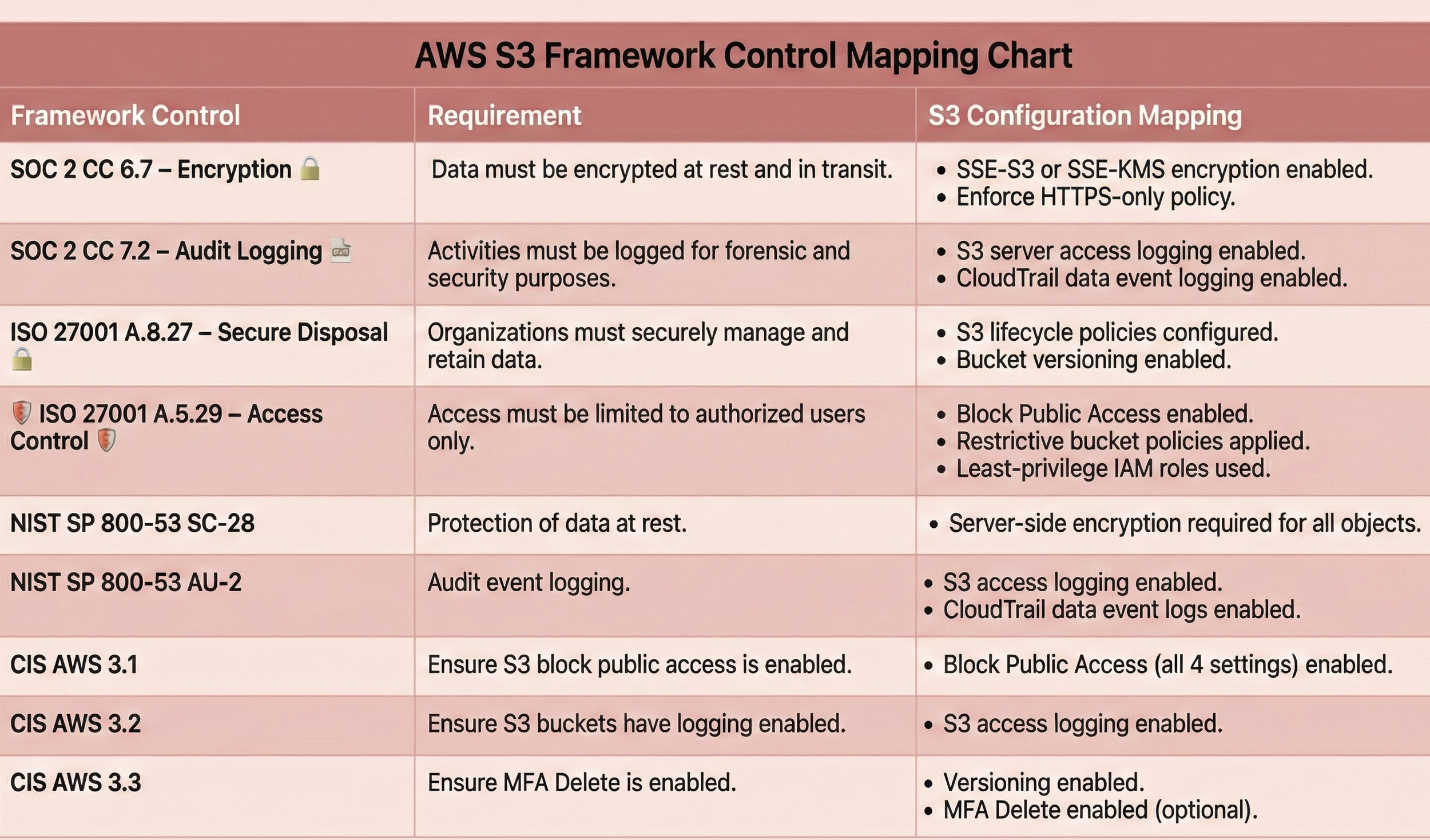
S3 Control Mapping
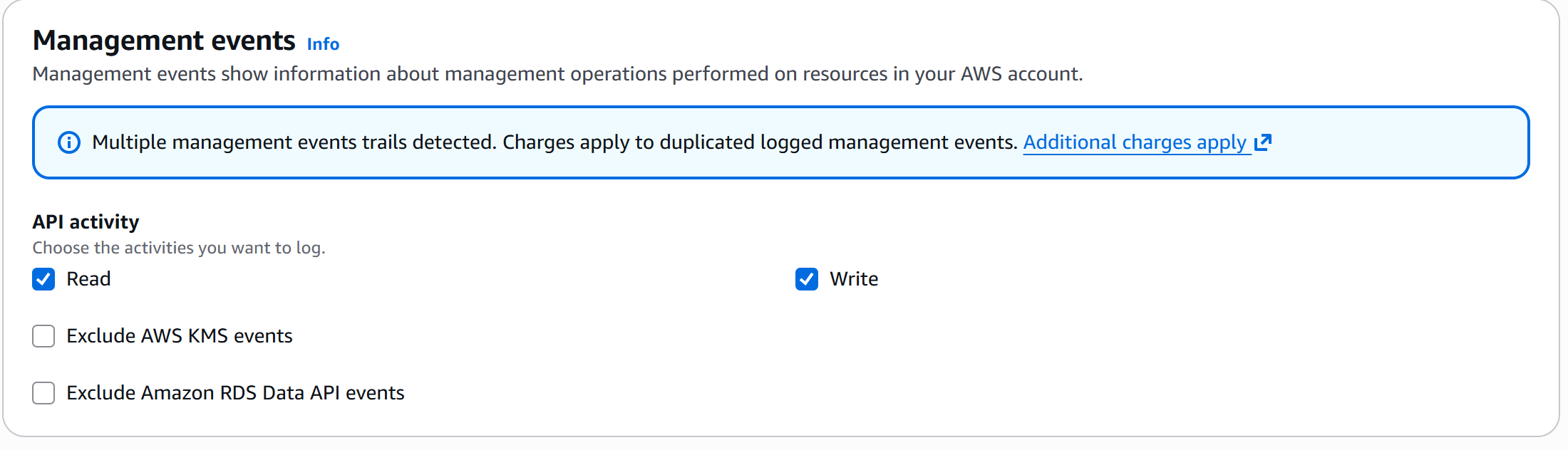
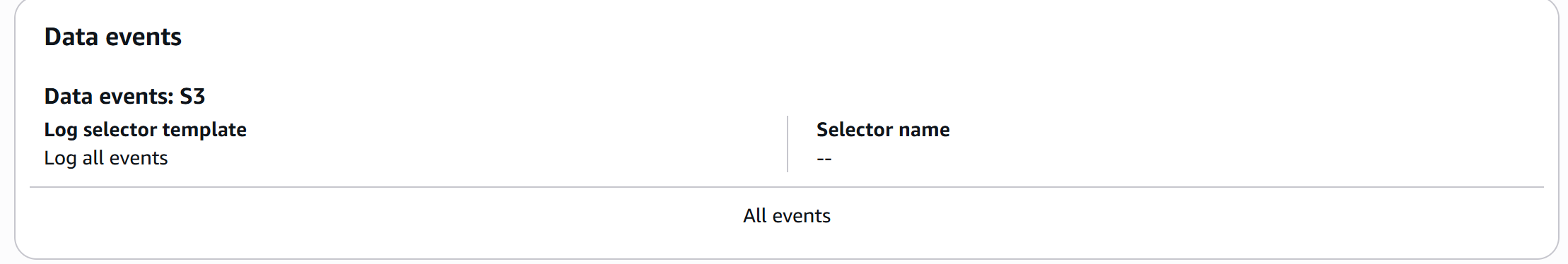
CloudTrail logging is fully enabled for both Management Events and S3 Data Events, providing complete audit coverage of administrative bucket activity and object-level read/write operations. Log file validation ensures integrity and authenticity of delivered logs, supporting forensic investigations and compliance requirements across SOC 2, ISO 27001, and NIST frameworks.
These S3 bucket configurations enforce secure-by-default settings across the bucket, ensuring alignment with AWS best practices and compliance frameworks (SOC 2, ISO 27001, NIST, CIS). This includes encryption at rest, blocked public access, versioning for recovery, and hardened access controls.